EdgeRouter VLAN isolation
In this post I will show you, how to create a VLAN with your EdgeRouter and how to fully isolate it from all your other networks.
The following configuration shows my VLAN setup for IPTV services, since the receivers do not need access to the other networks and an isolated network for IPTV can avoid trouble with multicast/IGMP. You don’t use IPTV? No problem, you could use the config to create a guest network or for other untrusted devices.
I’m using an EdgeRouter X, but this configuration will work on any other EdgeRouter. The general approach should even work on a UniFi router like the USG.
Update (15. February 2018)
I have completely rewritten the firewall configuration guide, since the first version had a substantial flaw: it will cut the access from the VLAN to your LAN, but the VLAN can connect to all router services. So, someone could open an SSH connection to your EdgeRouter and that’s bad.
If you have already followed the old guide, please delete the ruleset and use the new guide to create a proper firewall config.
Network Setup
10.0.0.0/24: home network oneth1192.168.1.0/24: management LAN for my DSL modem oneth010.0.1.0/24:eth2,eth3andeth4as switched ports on the EdgeRouter X
My management LAN is connected to the other networks via a custom NAT rule.
The main LAN consists of the three UniFi switches (US-8 and US-8 POE) and two UniFi access points (AP AC Lite). UniFi switches are fully supporting VLANs, so I can terminate a VLAN to any switch port within the network.
Why private class A networks? Well, why not? And I like short IP addresses.
But the management LAN is a private class C network? Yeah, I’m leaving the modem on it’s default network configuration to avoid trouble, if I ever have to reset it’s config. I like to experiment with other firmware versions. Currently I’m trying a firmware for australian ISPs. So far it’s working great and it disables some the VDSL error corrections from my ISP that can cause higher latencies.
Here we go
The IPTV VLAN will be on eth1 with VLAN ID 10 and will be terminated on a UniFi switch in the living room. If you need a guide, how to setup a VLAN on a UniFi switch and to assign it to a switch port, just click here.
Create the VLAN
-
Go to the dashboard of your EdgeRouter, click on
Add Interfaceand selectVLAN: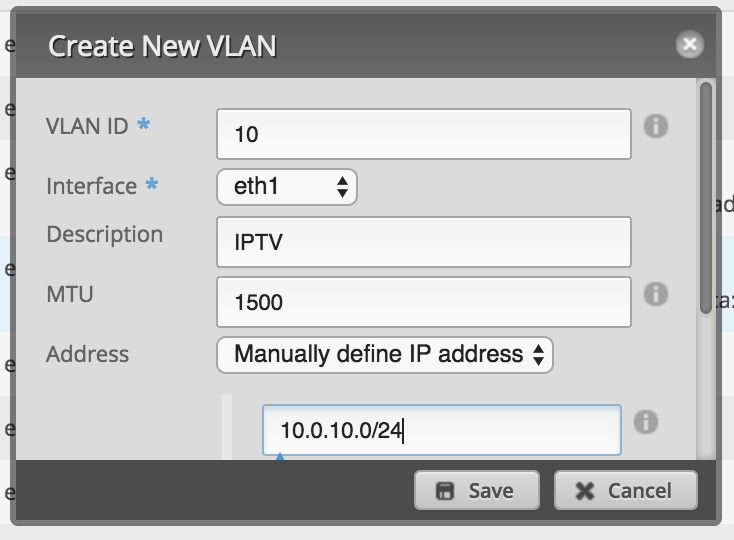
-
Go to section
SERVICESand clickAdd DHCP server: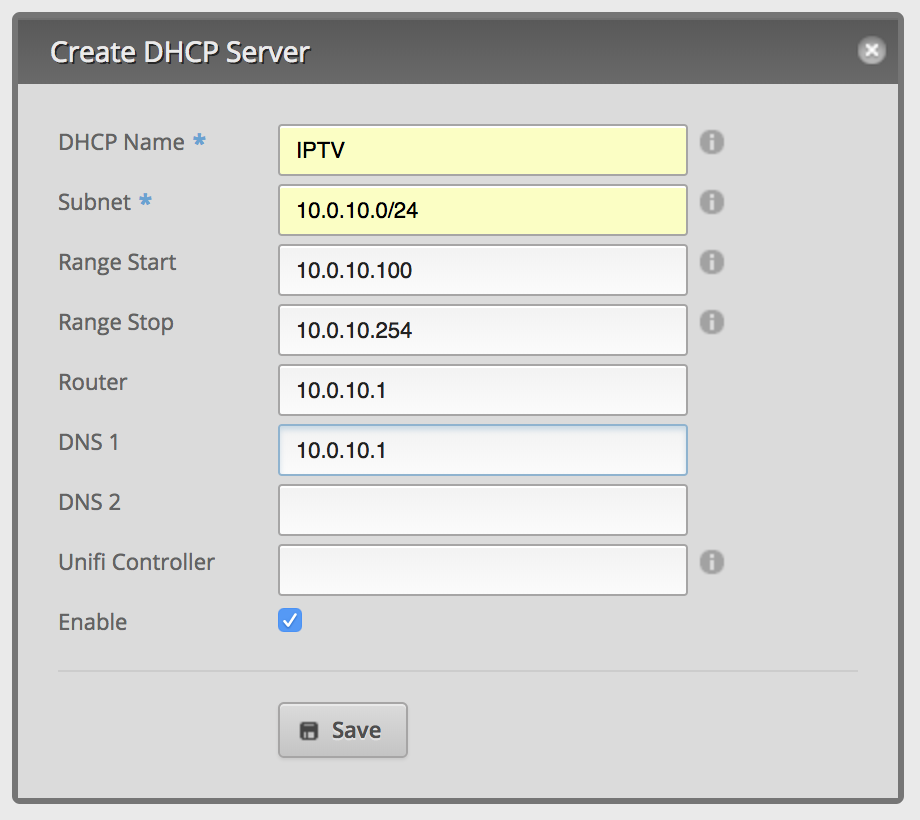
-
Stay in
SERVICES, go to the tabDNS,Add Listen interfaceand choose the interface of your VLAN: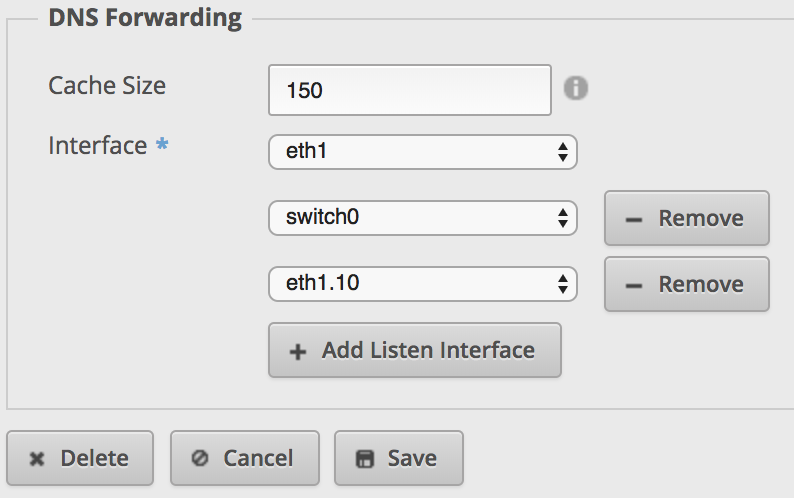
VLAN 10 is now ready to use, but it’s not isolated from the other networks. The EdgeRouter’s job is to route between networks. A device on VLAN 10 could access the LAN, your NAS for example.
Create network group
-
Go to
FIREWALL/NAT, then toFirewall/NAT Groupsand create a new network group: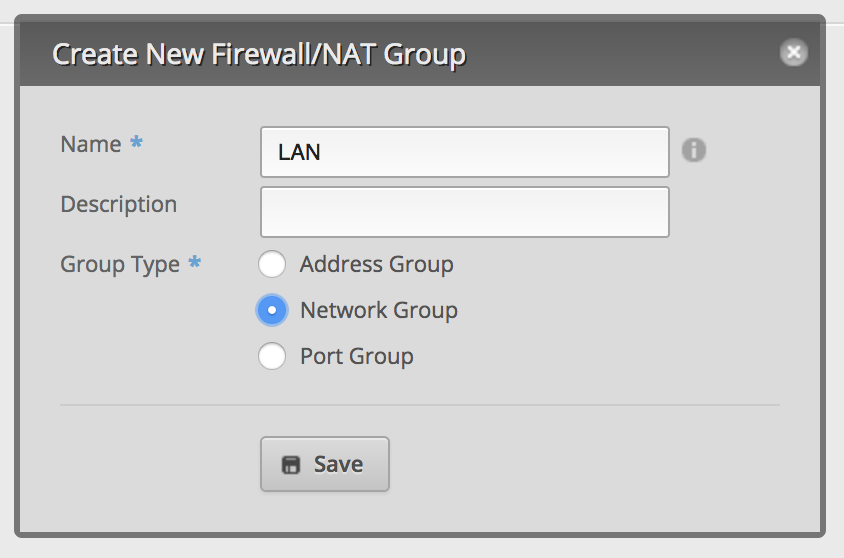
-
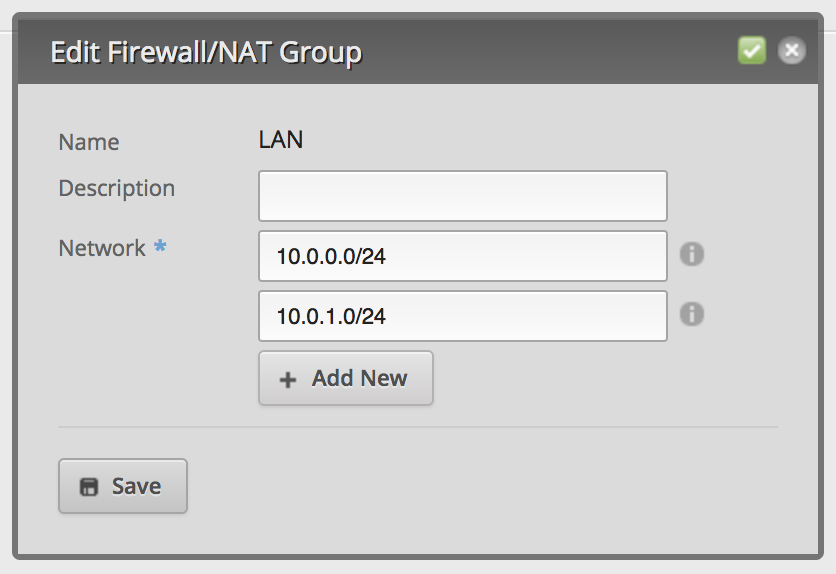
Edit the new network group and add all networks except the VLAN:
A quick guide to firewall directions
Before you create the firewall rulesets, you should know and understand the firewall ruleset directions:
IN: traffic entering the router from an interfaceOUT: traffic exiting the router to an interfaceLOCAL: traffic entering the router and destined to router itself (internal services, like DNS, DHCP, VPN etc.)
I will also provide a short explanation for each firewall ruleset and its direction.
If you’re having trouble to understand the directions, there is a very helpful diagram in the Ubiquiti forums.
Create firewall ruleset VLAN10_ISOLATION_IN
The following firewall ruleset blocks traffic into all networks of your network group, but will allow already established connections.
Direction IN means any traffic from eth1.10 to any other of your EdgeRouter’s interfaces.
-
Go to
Firewall Policiesand clickAdd Ruleset: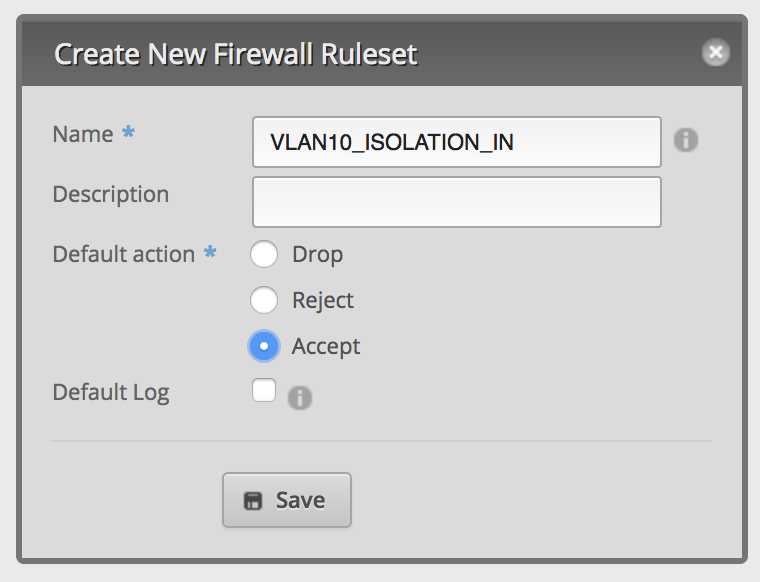
-
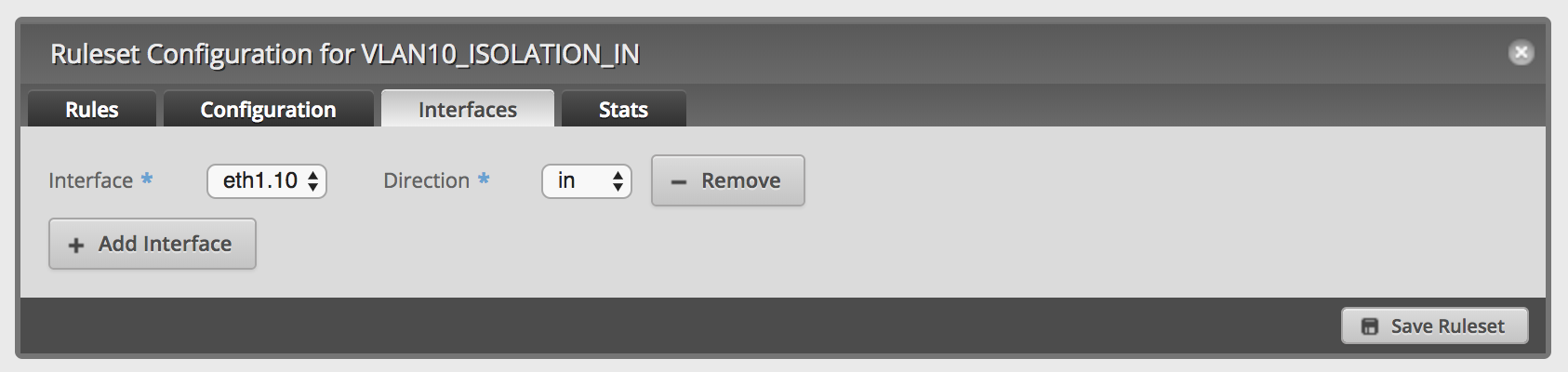
Edit the new ruleset and setup the interfaces:
-
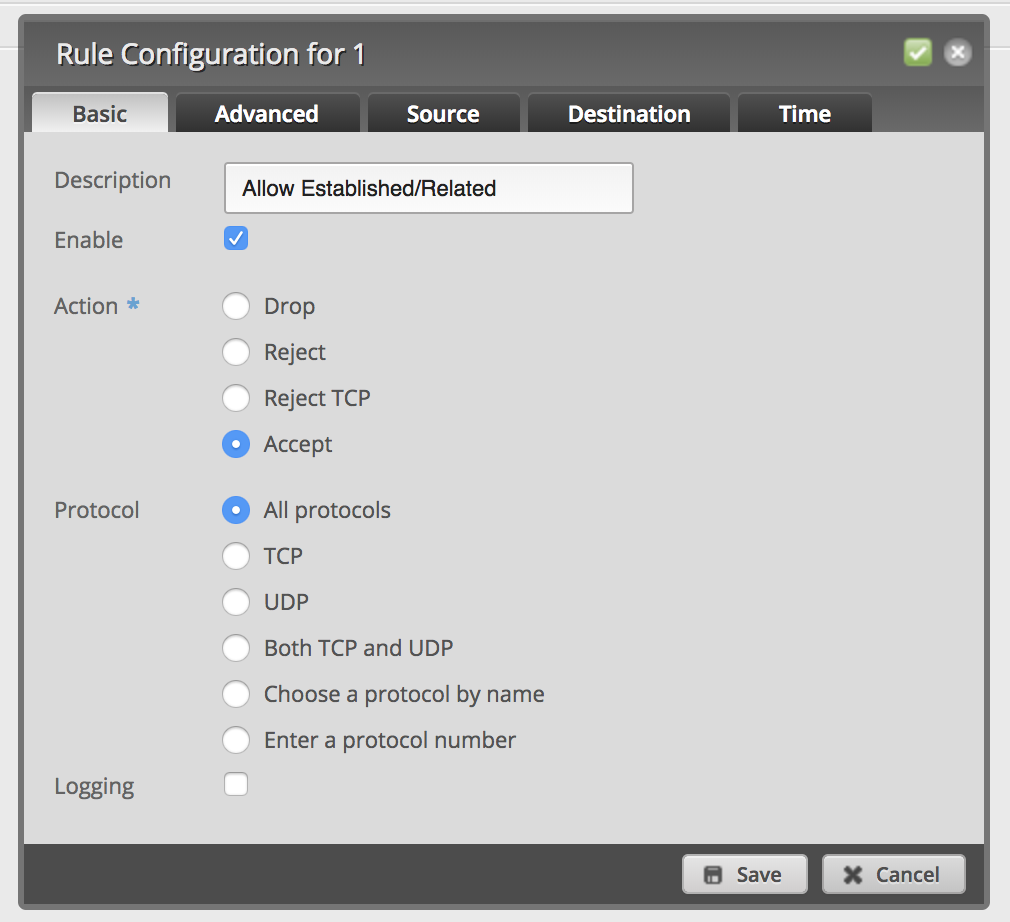
Add a new firewall rule to allow established and related packets:
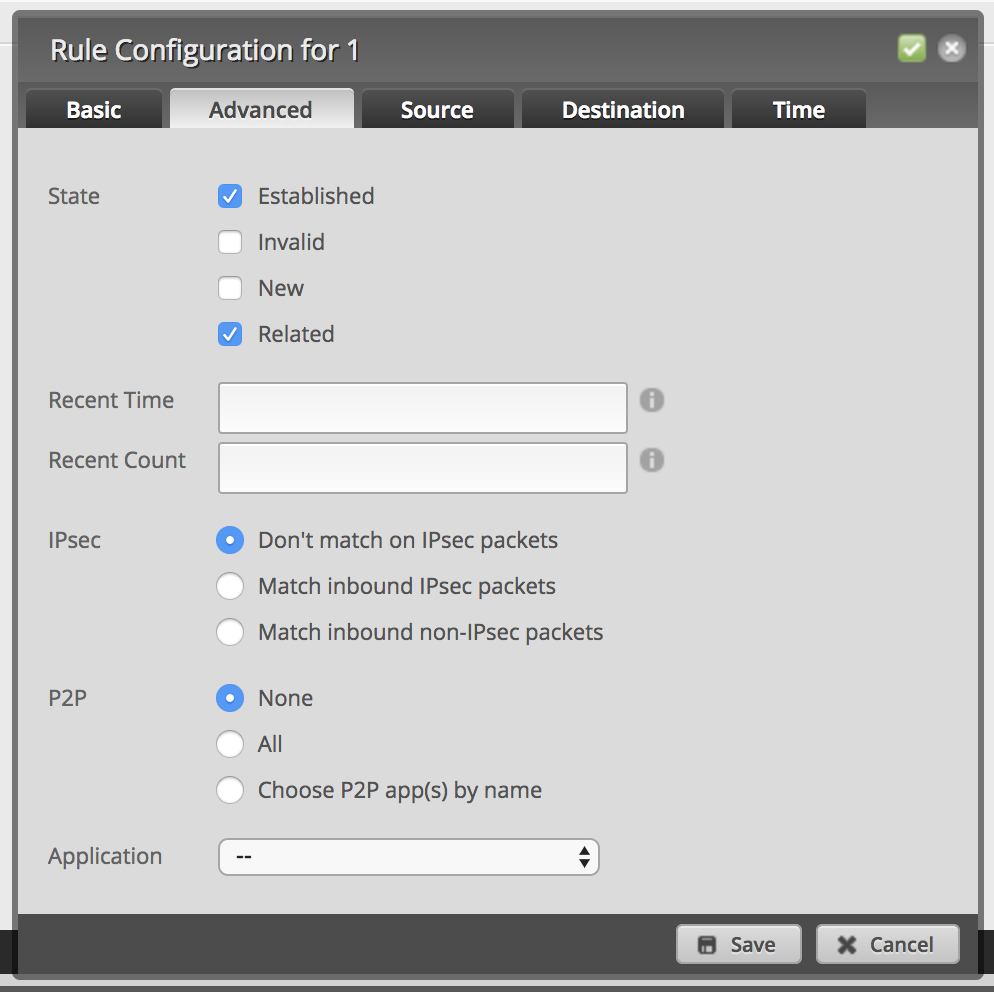
-
Add a new firewall rule to drop packets into network group
LAN: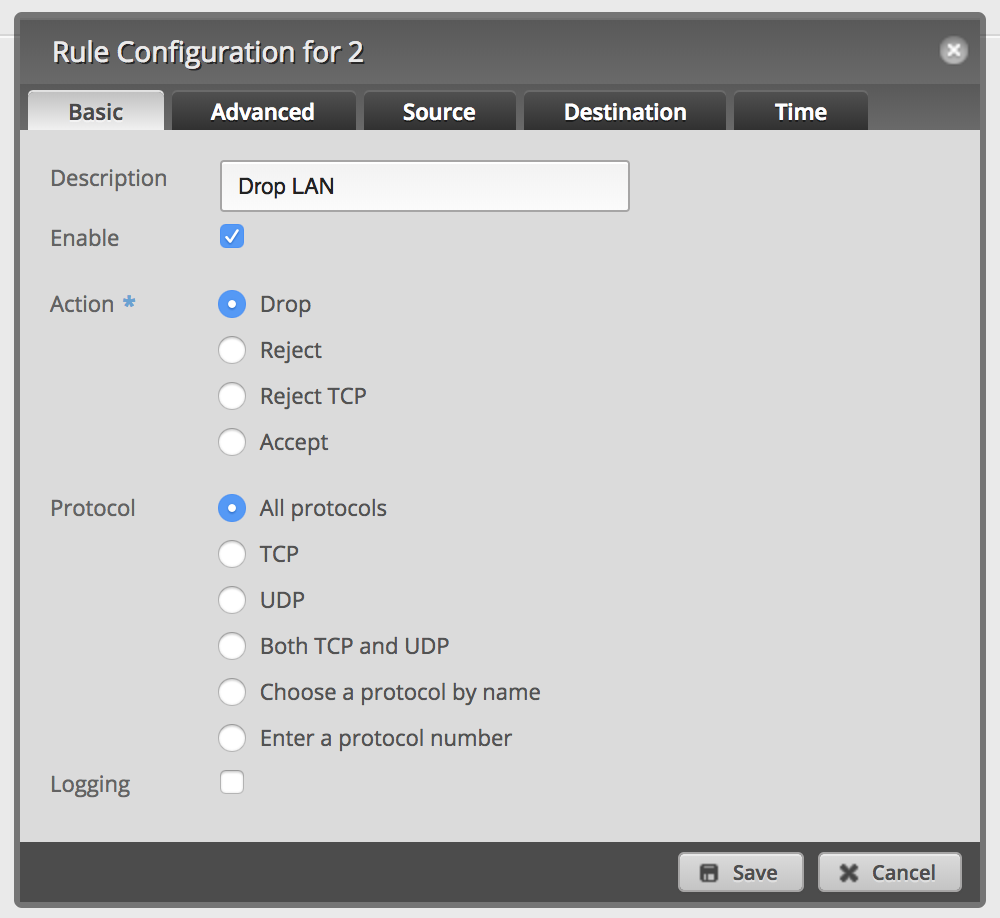
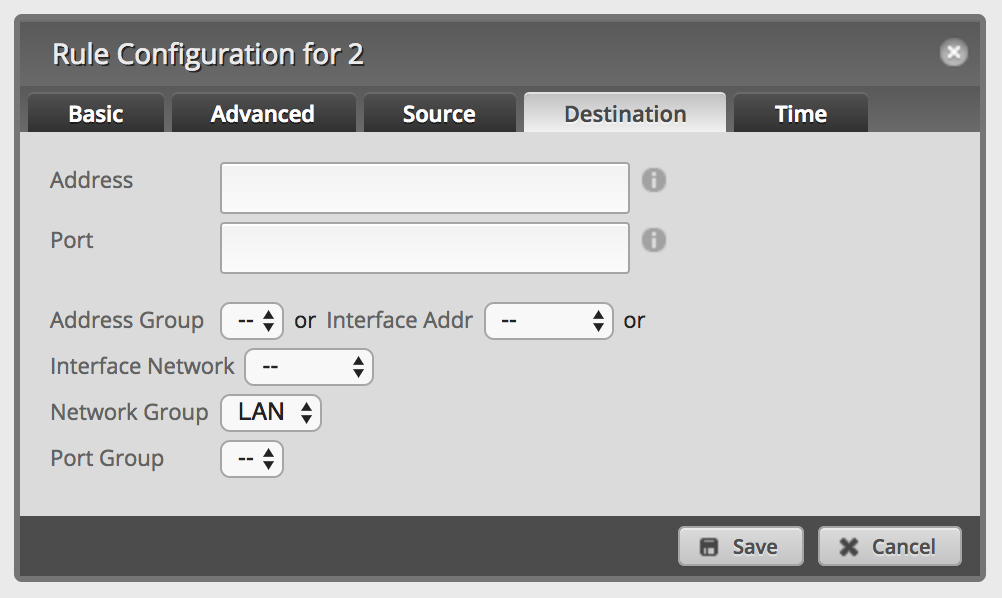
-
Your firewall ruleset should look like this:
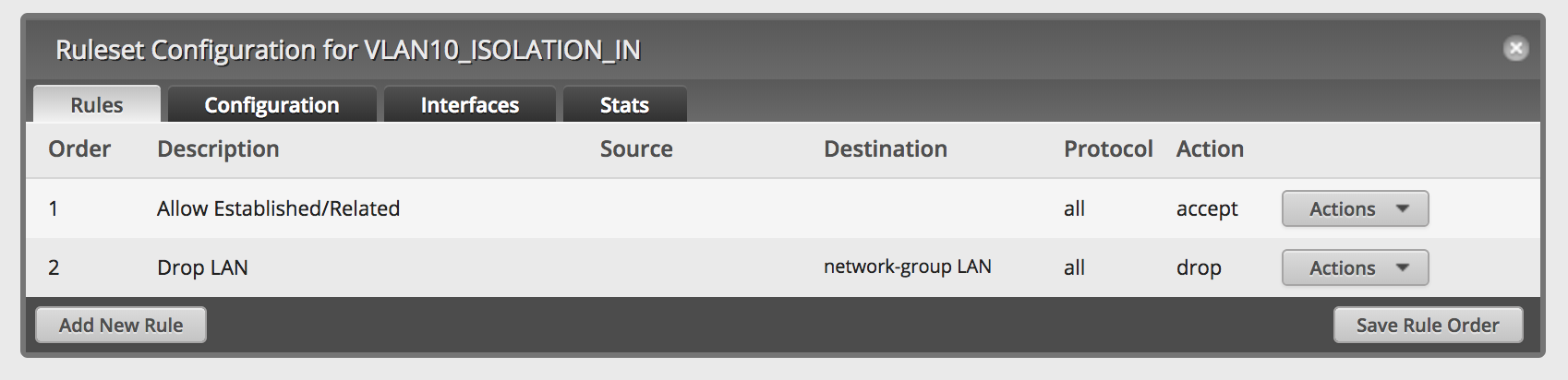
Create firewall ruleset VLAN10_ISOLATION_LOCAL
This ruleset will block any traffic to your EdgeRouters services, with the exception of DNS and DHCP.
Direction LOCAL means any traffic from eth1.10 directly to your EdgeRouter and its services.
-
Create another firewall ruleset like
VLAN10_ISOLATION_IN: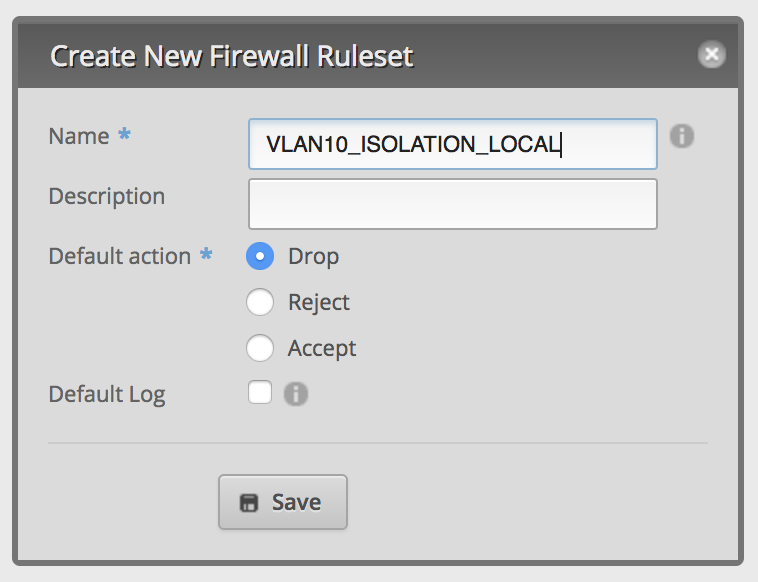
-
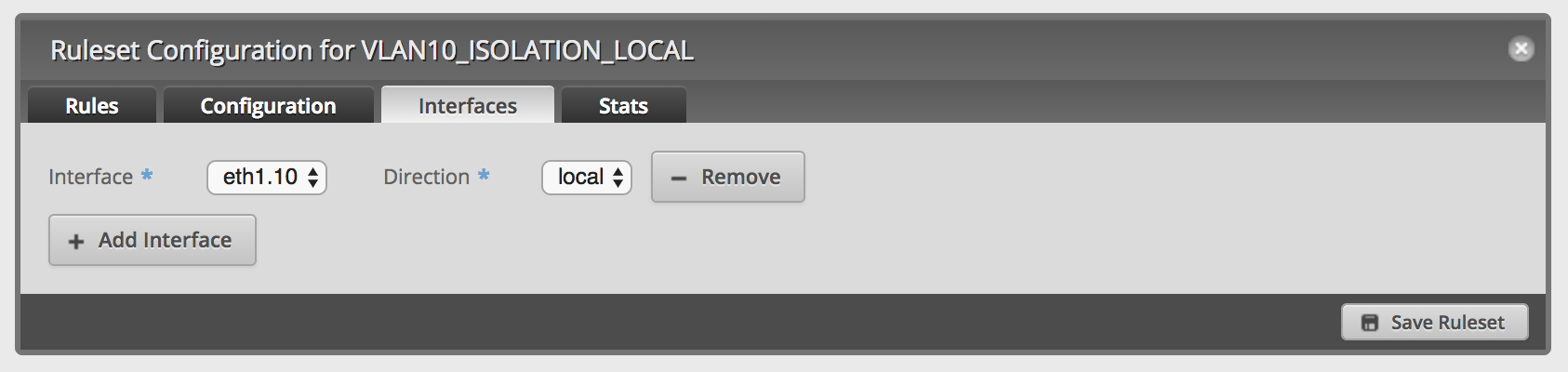
Edit the new ruleset and setup the interfaces:
-
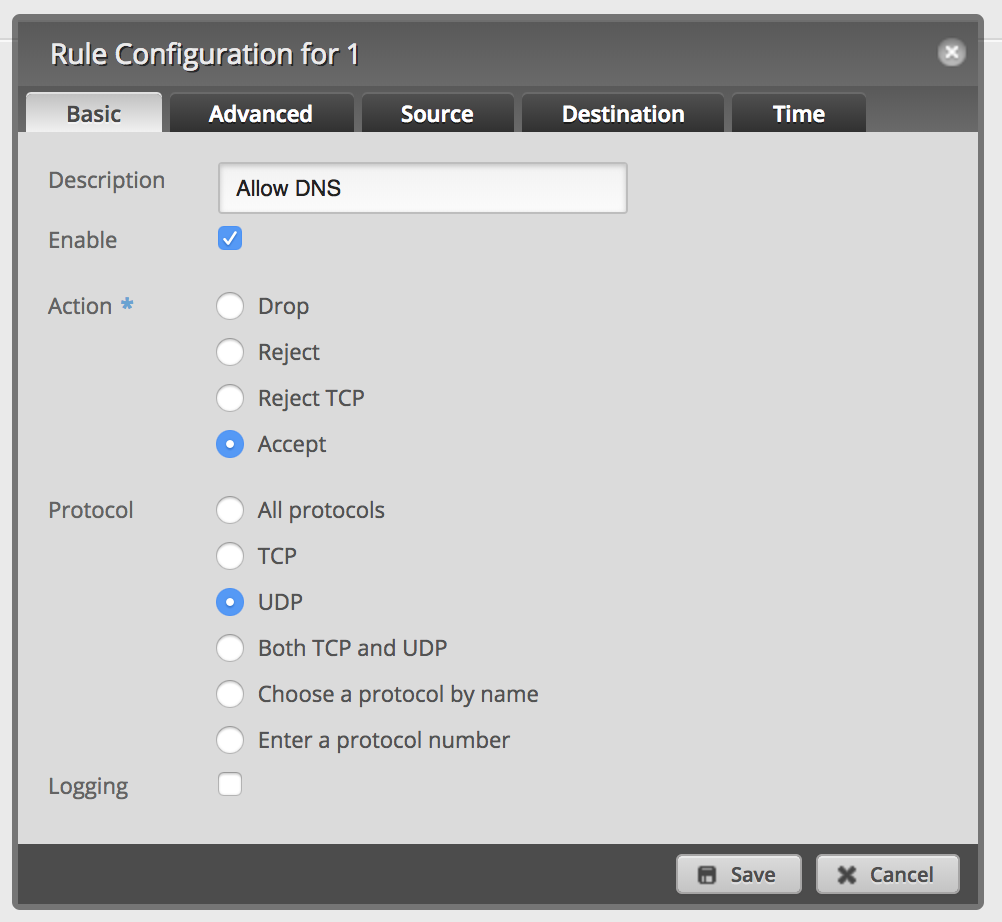
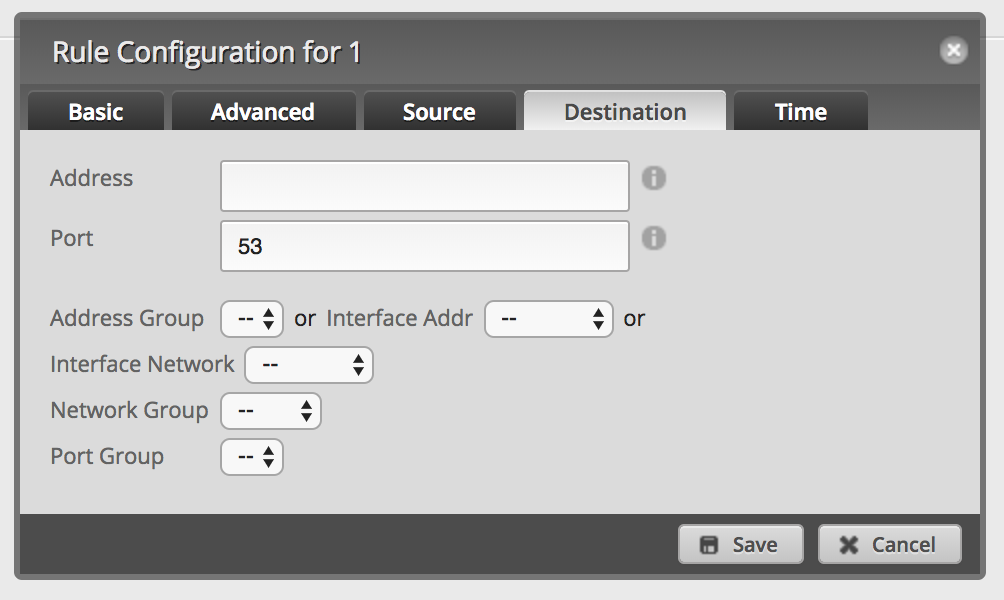
Add a new firewall rule to allow DNS:
-
Add a new firewall rule to allow DHCP:
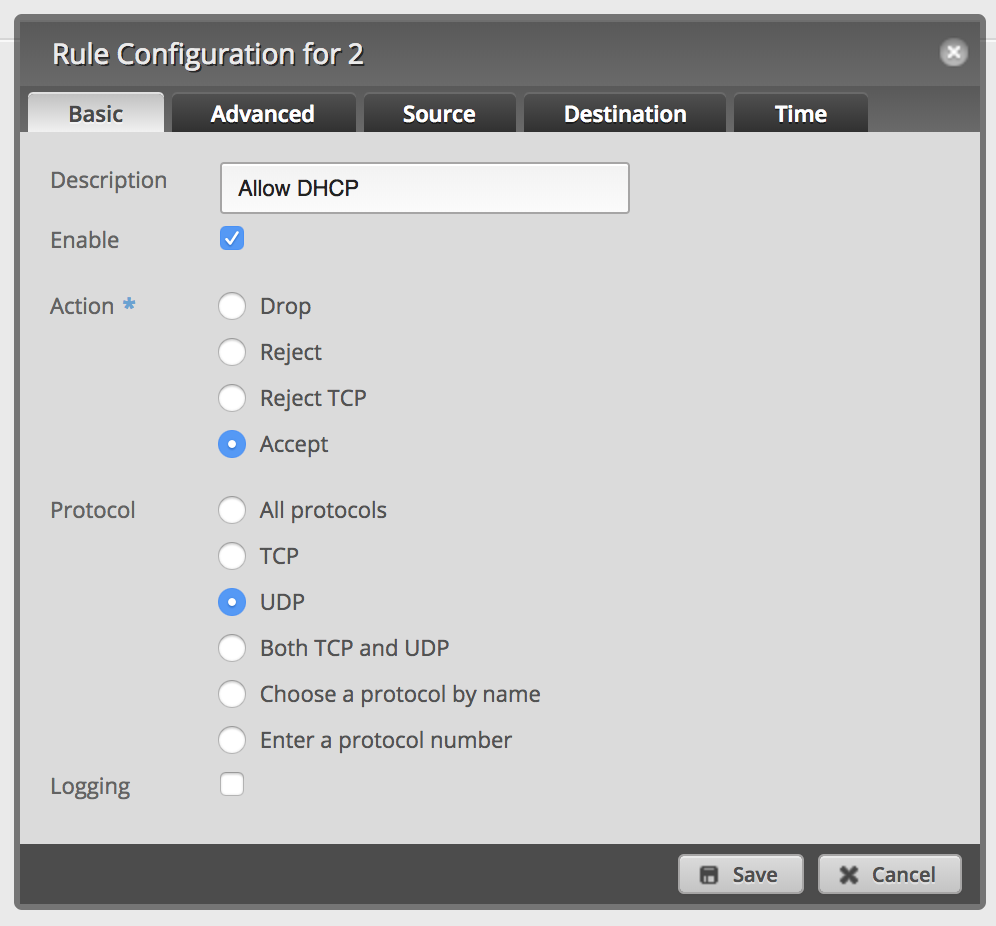
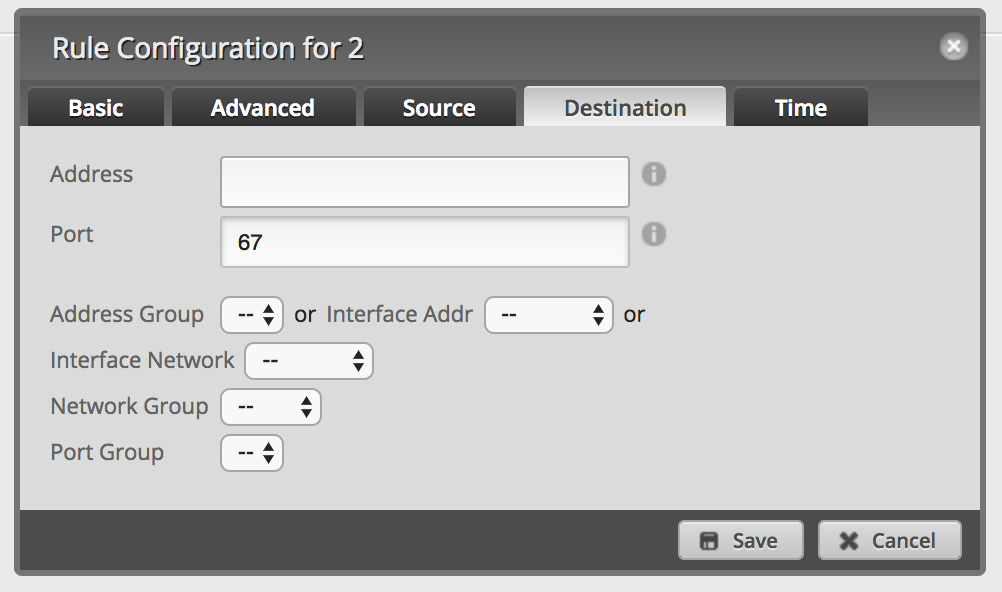
-
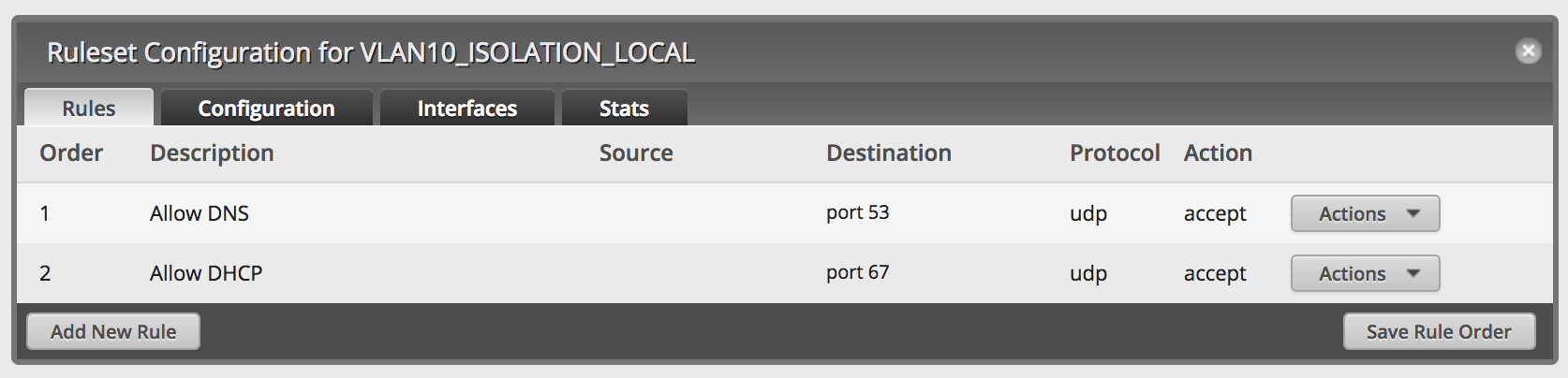
Your firewall ruleset should look like this:
Optional: assign network groups to custom NAT rules
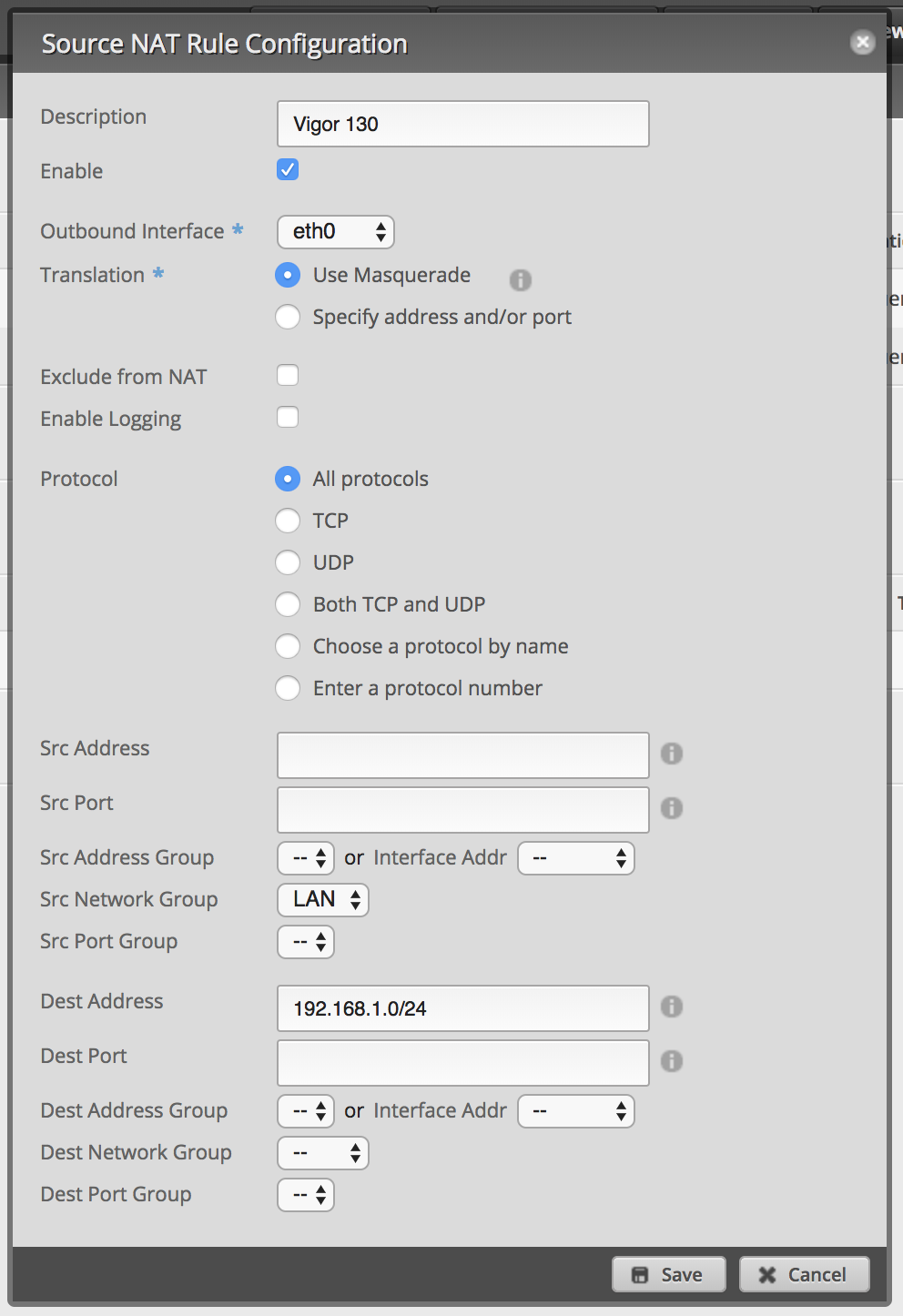
If you’re using custom NAT rules, you have to add your new network group to the rules to exclude the VLAN. Firewall rules alone will not isolate any networks from custom NAT rules.
That’s it. VLAN 10 is now fully isolated from all other networks. The firewall will drop all packages from eth.10 to the network group and my custom NAT rule will only work from networks of the group.